Keeping Your RDP Secure: Common Issues and Best Practices
Startups
Remote Desktop Protocol (RDP) offers a straightforward and convenient method for accessing systems remotely, but this convenience can be a liability for security if not properly managed. Without robust supporting controls and careful configuration, RDP can become a vulnerable entry point for cyberattacks.
The simplicity of remote desktop protocol technology makes it an attractive target for malicious actors. Common threats include brute-force attacks, man-in-the-middle attacks, and exploitation of unpatched vulnerabilities. These risks are particularly pronounced when RDP is exposed directly to the internet.
But don’t let these security challenges scare you away from using remote desktop services altogether, because RDP can be an amazing tool for meeting the demands of the digital workplace. Instead, think of them as a reminder of how crucial it is to implement comprehensive security measures. By following best practices and adding extra layers of protection, you can dramatically reduce your risks while still enjoying all the benefits RDP has to offer.
Here’s an overview of common RDP security concerns that you might run into, with actionable tips for how to secure remote access for your employees and yourself.
Remote Access: Secure or Exposed?

What vulnerabilities should we be the most concerned about? Where will our remote users encounter the most weaknesses? Here’s a list of the places you should start to tighten your secure RDP.
- User sign-in credentials. Most computers using cloud desktop hosting are protected by a password, and users sometimes make this password too easy to guess. Once the password is cracked and the hacker logs into RDP, he can move undetected in your environment and deploy malware. This also leads to ransomware attacks.
- Unencrypted communication. Sending and receiving data to RDP without any encryption allows hackers to intercept, modify, or steal your data, such as passwords, files, or keystrokes. Unencrypted communication can expose your system to man-in-the-middle attacks.
- Unrestricted port access. RDP connections almost always take place at port 3389. Hackers assume that this is the port in use and target it to carry out on-path attacks and other kinds of assaults.
- Malicious software. Running software that contains malware, spyware, ransomware, or other harmful code allows hackers to infect your remote systems with code that can monitor, damage, or encrypt your data, use your system as a bot, or as a proxy for other attacks. Malicious software can also compromise your system’s security settings or disable your antivirus or firewall.
- Outdated software. Using remote desktop software that is not updated for security patches enables hackers to obtain secure remote access or run harmful malware by knowing vulnerabilities and defects in your software. Outdated software also leaves your remote device open to compatibility problems, performance problems, or functionality flaws.
Best Practices for Securing Remote Desktop
Here are several tried-and-true best practices that can significantly bolster security on your remote machines. These range from fundamental steps like using strong, unique passwords and keeping your systems updated, to more advanced measures such as implementing multi-factor authentication and utilizing VPNs for those with privileged access.
1. Using strong passwords
Maintaining a secure RDP requires a policy of strong passwords for those accounts with remote access operated by authorized users. A strong password typically includes a mix of uppercase and lowercase letters, numbers, and special characters. The length should ideally be more than 10 characters.
2. Using two-factor authentication
Multi-factor authentication significantly improves account security. By requiring different forms of verification, such as a text message or an authentication app, MFA ensures that knowing the password alone is not enough to gain access to ip addresses. This is especially required with login attempts on a remote desktop, as the multiple factors present an additional obstacle for the attackers.
3. Updating your software
The fact that your Windows operating system is automatically updated with the most recent security changes is one benefit of utilizing Windows RDP vs. third-party remote administration tools. By turning on and monitoring automatic Microsoft updates, you can ensure that the client and server software are up-to-date. Make sure you have the most recent versions of remote desktop clients and that they are supported on other platforms. Older versions can have additional security issues and not support strong encryption.
4. Restricting access using firewalls
To restrict access to the remote desktop listening port (TCP 3389) you should install firewalls on your network connection (either software or hardware) to prevent unauthorized login attempts. It is strongly advised to use an RDP gateway to limit remote desktop access to PCs and servers. You can add the company VPN (virtual private network) address pool to your RDP firewall exception rule to facilitate off-company connectivity.
5. Enabling Network Level Authentication
By default, Windows 10 and Windows Server 2012 also provide Network Level Authentication (NLA). You should leave this active, as NLA provides an extra level of authentication on Windows servers before a connection is established. If you utilize remote desktop clients on non-supporting platforms, then you should only set up remote desktop servers to accept connections without NLA.
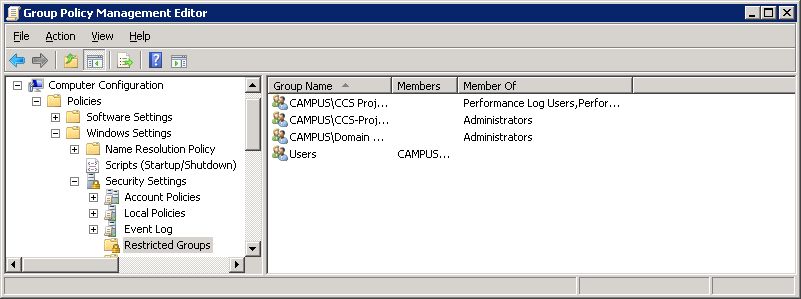
You can check by looking at the Group Policy setting. Use Network Level Authentication NLA to make user authentication mandatory for remote connections. The server that is hosting the remote desktop session has to have this Group Policy setting enabled.
6. Limiting users who can log in to Remote Desktop
All admins have default access to the remote desktop. If your computer has several administrator accounts, you should be restricting RDP access to only those accounts that require it, not all standard user accounts. Remove all administrative access if the remote desktop isn’t being utilized for system administration, and permit user credentials that need RDP service. Remove the local administrator account from RDP access and add a monitoring group for engineers who observe workstations remotely.
7. Setting an account lockout policy
By setting your computer to lock an account for a given number of incorrect guesses, you will prevent hackers from gaining access to your system with automated password-guessing tools (i.e. the brute-force attack). To set an account lockout policy:
Go to Start -> Programs -> Administrative Tools -> Local Security Policy.
Under Account Policies -> Account Lockout Policies, set values for 3 options. You can set 3 invalid attempts with 3-minute lockout timings.
Advanced Security Options
Advanced remote desktop security options offer a robust shield against cyber threats, ensuring that sensitive data and systems remain protected. By implementing these advanced measures, you can keep your RDP secure and significantly reduce the risk of unauthorized access, data breaches, brute force attacks, and other security vulnerabilities.
1. Using RDP logging and configuration tools
It is not advised to use other components, such as VNC or PCAnywhere, as they might not have the correct level of network security. Logins via RDP are audited to the domain controller auditing system, as well as the local security log. When reviewing the local security logs, look for anomalies in RDP sessions, such as attempts to log in using the local Administrator account. To guarantee a secure and uniform RDP configuration on all of your servers and desktops, utilize GPOs or other Windows configuration management tools whenever feasible.
2. Forbidding direct RDP access to clients or servers out of the company
It is strongly advised against leaving RDP (port 3389) open to networks outside of your company, as this is a known attack vector. After setting up an RDP gateway, hosts should be configured to only accept RDP connections from the gateway host or, if necessary, business subnets. In this way, you will enhance security without allowing anyone to exploit RDP vulnerabilities.
3. Using RDP Gateways
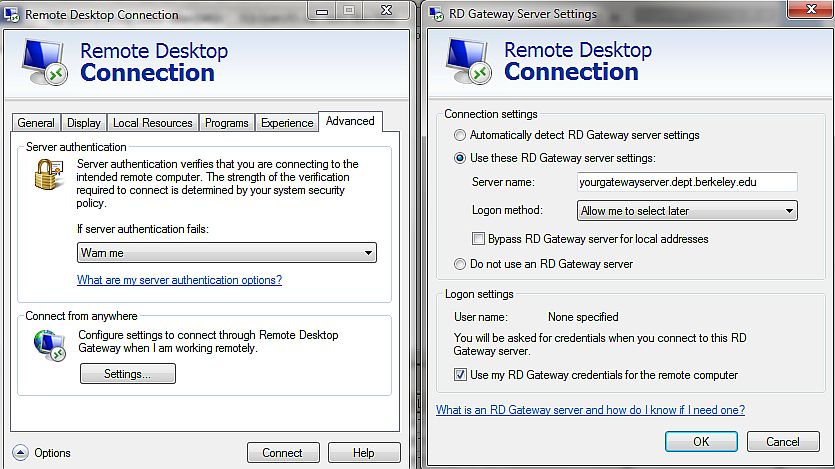
The use of an RDP gateway is highly advised. It facilitates secure remote desktop connections via a single gateway server while limiting access to remote desktop ports. All virtual network computing services on your desktop and workstations should be disabled when utilizing an RDP gateway server, so access is only achieved through the remote access solution. The client is connected to the remote desktop service to the target machine by the RDP Gateway, which listens for RDP requests over HTTPS (port 443).
4. Tunneling RDP through IPSec or SSH
Tunneling RDP connections over IPSec or SSH allows you to add a layer of authentication and encryption. Then employing an RD Gateway is not necessary. You can utilize SSH tunneling for Remote Desktop connections if there is an SSH server available. Since Windows 2000, IPSec has been included in all versions of Windows; however, Windows 10 offers significant improvements in management and usage.
5. Changing the default port
It is helpful to change the listening port to hide from hackers who gain unauthorized access by searching the network for machines using the default RDP session port (TCP 3389). This provides a strong defense against the most recent RDP worms, such as Morto. You can do this by changing some registry keys. Replace 3389 with a different listening port, and don’t forget to change firewall rules to reflect the new port.
Conclusion
The human factor is also a big issue that can compromise remote desktop security. To avoid all risks, your employees should follow best practices, such as logging out when not in use, locking their screens, using a password manager, and educating themselves about security practices on all remote desktop sessions.


